Our Process & Partner Toolkit
At Cyber Knowledge Partners, we operate as a strategic extension of your Board—delivering tailored cybersecurity and AI advisory that links risk governance directly to business performance. Our process is built to transform complex risk into boardroom clarity, empowering Directors to lead with confidence in an evolving digital landscape.
We do this through a structured suite of services:
* Executive Briefings that enhance Board preparedness and resilience, including tabletop exercises, incident response readiness reviews, and tailored dashboards.
* Regulatory and Compliance Support that keeps leadership ahead of shifting mandates, with curated briefings on evolving standards such as SEC rules, GDPR, and the EU AI Act.
* Crisis Navigation and Reputation Management to prepare and guide Boards in protecting stakeholder trust and fulfilling fiduciary obligations during cyber incidents.
This integrated approach enables Boards and CEOs to oversee cybersecurity not as a siloed technical challenge, but as a strategic function critical to resilience, compliance, and enterprise value..
“In a world connected by endless signals and threads of data, vigilance becomes our strongest firewall against unseen threats.”
— Anonymous Cyber Security Expert in the Intelligence Community
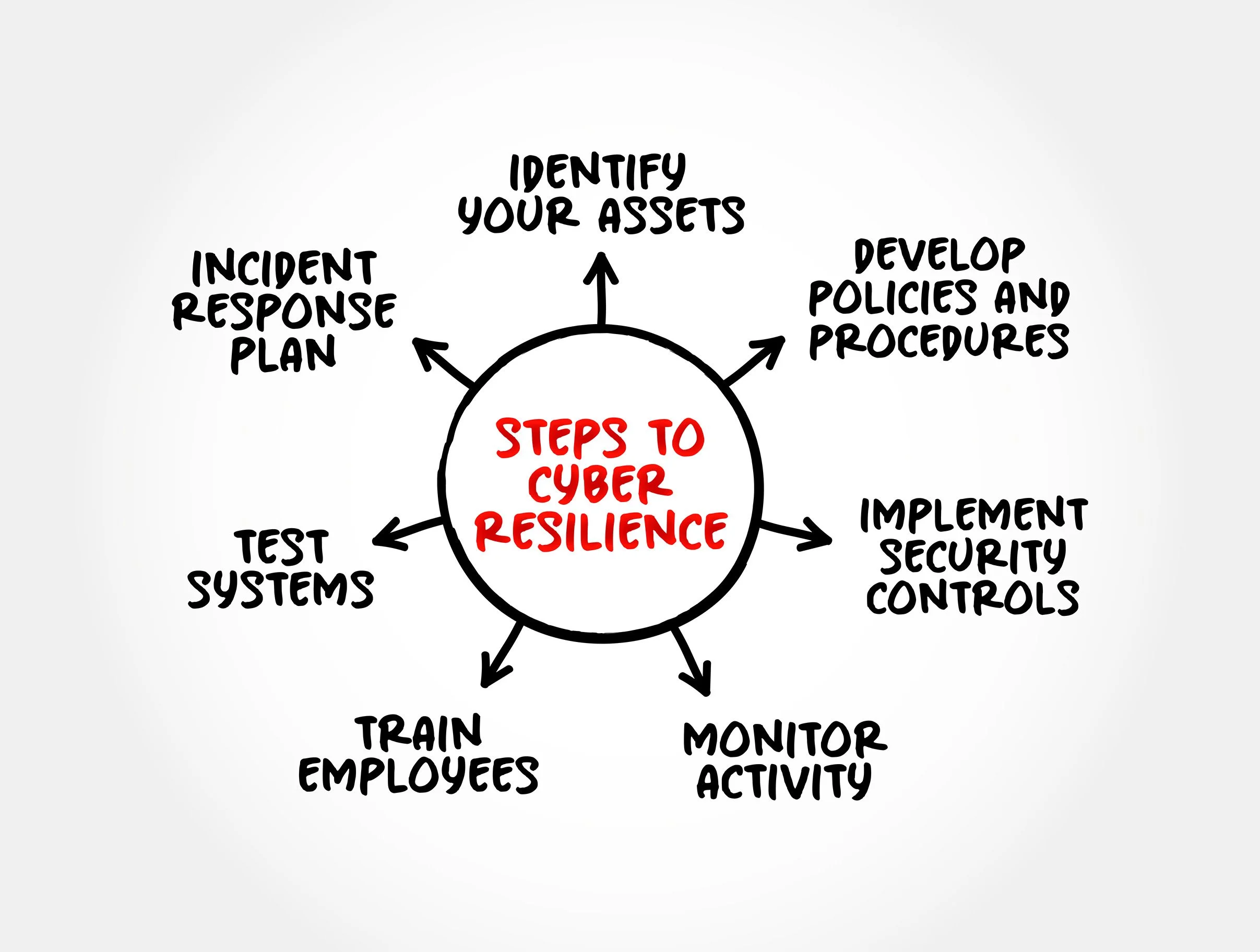
Cyber Resilience
& Business Continuity Roadmap
Risk Management and Risk Mitigation
Identification and Assessment of Risks
Employee Awareness Programs
External and Internal Communication Plans
Threat Awareness and
Industry Impact
Update Ongoing Threat Landscape
Review Industry Incidents
Ensure Compliance
Recovery Strategies
Maintaining Robust Communication Protocols
Rebuilding Market Trust
Integrating Learnings
Cyber Resilience and Process Investments
Ongoing Evaluation of Advanced Security Tools
Implement Security Controls
Create a Risk Management Framework
Business Strategy Integration
Embedding Security into Organizational Culture
Aligning Security Objectives with Business Priorities
Navigating Complex Threats while Maintaining Operational Integrity